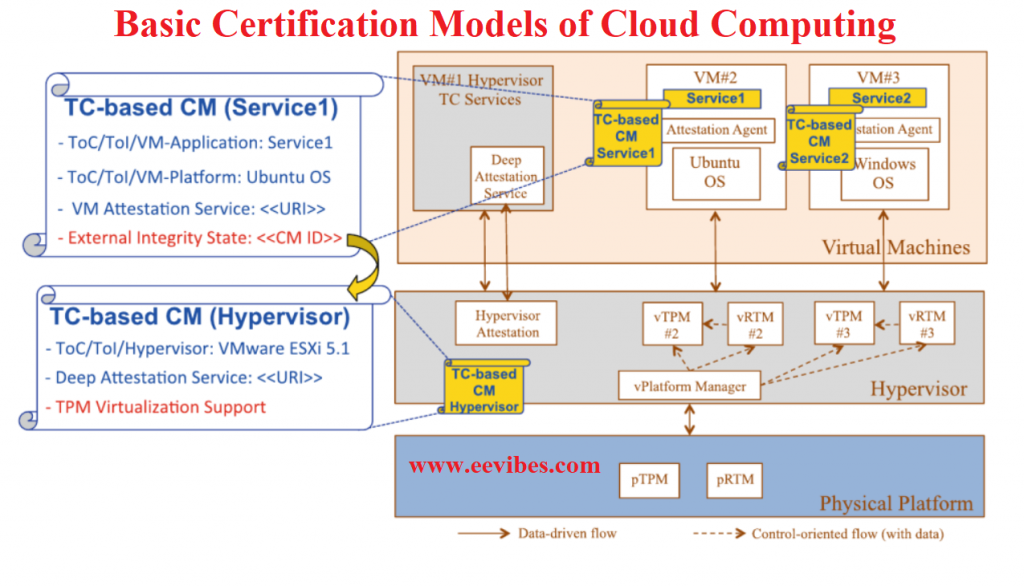
Introduction
There are three basic certification models of cloud computing that are supported by CUMULUS. These are:
- Test-based
- Monitoring-based
- Trusted Computing-based
In this article I will describe a meta-model to express common elements across all cloud management infrastructure (CMIs). This approach simplifies the processing of CMIs by infrastructure components of CUMULUS. Also it will ensure uniformity of high level structural representation across different types of certification.
The main components that each individual CMI include are:
Security Property
It defines the security property that need to be certified by the security model. An extensive catalog containing security properties has been defined by CUMULUS.
Target of Certification (ToC)
Parameters of certification are defined by ToC. Instance of the services and instance of the cloud stack are identified by the ToC. This usually includes the components definition, connections, and many other things like that. Hence ToC can determine that the consumer’s requirements of certification are met or not. This detailed certification is actually very helpful for consumer.
Life Cycle
After the issuance of the certificate, evolution of certificate is defined by the life cycle. Many decisions like certificate suspension, cancelation, and expiration are usually taken asynchronously and offline by the certification authority. For example in case of newly discovered vulnerabilities this life cycle is helpful. In case of cloud life cycle certificate is managed at run time. It happens on the basis of evolving evidence. That is why the feasibility of static intervention of certification is not possible. We need to maintain high level certificate of life cycle. The life cycle elements include the vocabulary of the certificate such as expiration, and issued, which simplifies processing and comparison across life cycle specifications of different CMIs. However, we can define another extended CM certificate just for the flexibility.
Also check:
Most Common Advantages and Disadvantages of Cloud Computing?
Signature
The certification framework’s signature on the CMI is provided by the signature element, which was delegated by the certification authority. In order to establish the chain of trust, the signature is required.
Monitoring Based Certification models of Cloud Computing
By monitoring the operation of cloud services continuously, evidences are collected. Then by their analysis, the CULMULUS infrastructure is used for generating certificates. In order to use it to its capacity, it is required to define a monitoring based certification model (MBCM). This model specifies:
- The security of cloud to be certified (ToS).
- The security property for ToC to be certified.
- The assessment scheme that will define the criteria for the issuance of the certificate.
- Validity test regarding the certification.
- A life cycle model which will describe the model of issuance of certificates.
The three main elements that are necessary for specifying and executing MBCM are:
- Security Properties
- Models of life cycle
- The evidence of sufficiency conditions
Security Property:
The security property is usually expressed as follows:

Target of certification and assessment scheme
The assessment scheme helps to collect the evidence for the issuance of certificate. The condition for the sufficiency of evidences includes:
Minimum period for which ToC is monitored.
The minimum number of events of monitoring.
Who are the representative of monitoring events.
The certification model must include the specification of model of the expected behavior of ToC. The operation of ToC may be done at each state in its operation in any sequence, and it is possible to predict the likelihood of each execution by expressing the predicted behavior model for ToC as a probabilistic state transition model.
I will add more in this article later on.
Also read here