
Table of Contents
Introduction
This article is about ZigBee modules that focused on the following given areas:
- This system is used to establish a secure communication between two soldiers or authorities.
- This system is non-hackable and highly secured for communication.
- This system is designed to double encrypt the message and to ensure that any kind of leakage can be avoided.
Today, the Pakistan’s main mission is to spot and prevent the entrance of terrorists, weapons of mass devastation, and illegal partners in the country. Hence, armed men need highly secured communication having encryption and password protection. This structure must be non-hackable and should provide safety while communication.
The objective of this system is to create a secure communication between two soldiers. Because any kind of message leakages, illegal access of data and frequency hacking can directly allow admittance to the private messages and missions of the armed forces to opponents.
Today’s communication system used by our soldiers is walkie-talkie. This works on frequency transmission for passing the message. As through numerous methods this frequency (in some cases) can be hacked, a more protected communication model is essential that will particularly encrypt the message and thus any kind of leakages can be evaded.
Review
-
et all:
He present that Arduino is an open source electronic circuit board that uses a microcontroller ATmega328P-PU. The type of Arduino used was Arduino Uno and the encryption technique was substitution. The substitution encryption technique was applied for data communication security and its application in Arduino Uno can be used in asynchronous serial communication.
-
Ievgeniia kuzminykh.et all:
He focus on ZigBee wireless technology and testing ZigBee end devices in order to see how transmission range impacts on quality parameters. ZigBee Remote Control protocol has various advantages among systems offering low power transmission, high security and high scalability etc. In this paper, testing of ZigBee modules was preformed through the use of the software X-CTU.
-
Vivek Negi et.all:
He theorized that the security in terms of Networks have turned out to be more significant to Military and personal computer users. Since various types of threats are present for data sent from sender side over internet till it reaches to receiver. By encrypting the data we can save it from attacks like eavesdropping.
- Akmal Nurhananie Abd Rahman.et all:
In this paper author presents the application development conducted for Android devices and the current results achieved. The project focused on using ZigBee-based technology. Peer-to-Peer (P2P) is also a very popular type of network communication for file sharing, where the data transfer is faster as it does not need to pass through the services of a server to share files and data.
Methodology
The proposed system has two users one is sender and the other one is receiver. The sender system consists of various components:
- An android device with an android application installed on it.
- A Bluetooth to receive messages from the android device.
- A ZigBee module is used to transmit the received message to the receiver side.
- An Arduino board and a microcontroller to install all the components. The microcontroller is an Atmel 8-bit AVR RISC-based microcontroller combining 32 KB ISP flash memory with read-while-write capabilities, 1 KB EEPROM, 2 KB SRAM, 23 general purpose I/O lines and 32 general purpose working registers. The range of operating voltage for this device is 1.8-5.5 volts.
As shown in Fig.1 (a) when the application opens by a sender, in the background a timer of 5 minutes gets started, which logs out the application automatically when detects inactivity of five minutes. Also, the application is protected by password. If more than 3 times wrong password is inserted it automatically stops the functioning of the device. After successfully login, now the sender has two options either to type the message or there is a speech to text recognition API installed on the application that can convert the speech to text. Now the Arduino board which is connected to android device via Bluetooth gets the transferred message. The message sent from android device to Arduino device gets 8-bit SSL encrypted. Which further gets transferred to the receiver’s end via Zigbee which has 128bit AES encryption.
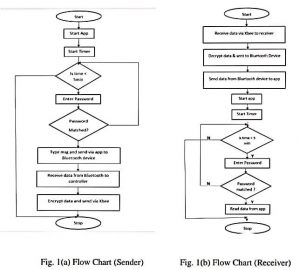
As shown in Fig.1(b), when the message is received by the Zigbee receiver, the message is 128bit AES encrypted which is further decrypted by the Zigbee module. Then the message gets forwarded to the android application via Bluetooth where a decryption of 8 Bit SSL is again done. Now, finally the receiver gets the message. The receiver needs to log in the device to view the message as the device is password protected.
System Architecture
Explaining the System Architecture as shown in fig,
- The National Security Model contains two Arduino Microcontrollers with SSL which is basically used for encryption-decryption.
- Zigbee is installed for the communication between two Arduino devices.
- Keypad is used for typing the required message.
- LCD (Liquid Crystal Display) is used for displaying the message that are connected to microcontroller. The connection between an android device and Arduino board is through Bluetooth.
- For sending and receiving the messages, android application is installed in the android device.
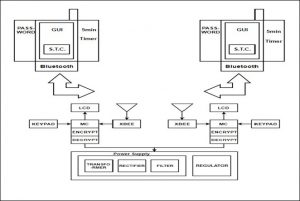

Once the message will be sent by the sender instantly by utilizing his android application installed in the device, the message will get encrypted through SSL. And, as soon as the encrypted message will proceed to the microcontroller, it will again get encrypted via Zigbee. The sender’s Zigbee module receives the message from the microcontroller ZigBee module once. This is how double encryption is achieved through such manner.
The same process will be followed in descending approach on the receiver end. And, the receiver can see the message once it gets decrypted.
Result and Discussion
Zigbee is used for initiating communication between devices which can have a range from 100m to 64km. This range of Zigbee depends on the Xbee module used. The system of military communication consists of three major devices which are Sender device, Receiver device, and A mobile application installed on both the devices of sender and receiver. A unique password is set up on the device to logged in by the sender.
In result of 5 consecutive failed attempts to login, a permanent broken connection will be observed between mobile and the device. Message sent by the sender will reach the sender device via Bluetooth after the successful login. The device should be in the Bluetooth range to transmit the message. So, it would be preferred to keep the device in the pocket or bag of the soldier. This encrypted message will once again be encrypted and with the use of Zigbee module, this encrypted message will be sent. The Zigbee module has digital signals which are difficult to intercept in between. Once, the receiver device gets the message, the process of decryption starts in the reverse manner on encryption. And, afterwards the message is forwarded to the mobile of the receiver, which will be viewed on successful login. Once the message is seen, it will automatically be deleted after 5 minutes.
Conclusion
At the areas where there is no internet or either low connection of internet, a system is designed to establish an encrypted and secured communication way within military comrades at the country borders. So, a highly secured communication way can be attained between the two officials through this system. A highly secured and a non-hackable encryption keys are developed in the system with the integration of embedded systems and an enhanced digital security level. In result, the system will be double encrypted to be more securable. Firstly, with the SSL and secondly with Zigbee.
Future Work
This system is just a model for transmitting securable messages. The current system can be increased from point to point communication to broadcasted communication in a case needed. Therefore, a large network of communications can be executed for more than two people. For improving and upgrading the system, a long range facility and an increased encrypted level can be attained by using double encryption method. The higher the range of Zigbee module, the more encrypted and secured will be the communication.
Also read here
- Embedded Systems Future: Design of optimized Energy Metering Devices
- What are the important parts of an embedded system?
- How to do the software power optimization in embedded systems?
- Revolution brought by Embedded Systems with Data Analytics
- what are the practical applications of embedded systems?
- what are the challenges in embedded systems design?
- What is the Linux Operating System?
- Define Cryptic Mining for Automatic Variable Key-based Cryptosystem