
Introduction
Define Cryptic Mining for Automatic Variable Key-based Cryptosystem. This article examines and analyses the state of symmetric cryptosystems as well as the evolution of automatic variable key cryptosystems. It explains the framework of the AVK model and how to extend it using a parameterized method. The evaluation of a cryptosystem from a cryptanalyst’s perspective has been offered. The work establishes the “Cryptic Mining discipline.”
The AVK method is useful for low-power secure device communication, which is a key element of the internet of things. This paper examines and analyses the state of symmetric cryptosystems as well as the evolution of automatic variable key cryptosystems. It explains the framework of the AVK model and how to extend it using a parameterized method.
The evaluation of a cryptosystem from a cryptanalyst’s perspective has been offered. The work establishes the “Cryptic Mining discipline.” The AVK method is useful in low-power secure devices.
In the context of the internet of things, low-power devices and device-to-device communication are critical (IOT). The system’s long-term viability will be determined by the security of these devices, as well as a balance of power efficiency. The Automatic variable key is gaining popularity and finding use in low-power technologies. Because of the key’s short life span and compact size, it’s a good contender for energy-efficient secure communication.
The addition of a parameterized key-based cryptosystem to the design of an efficient cryptosystem will add another layer of protection. We present the concept of an Automatic Variable Key, a framework for key exchange based solely on parameters, its importance, and benefits, as well as an analysis of an AVK-based framework from the standpoint of hackers and crypto-analysts, as well as its evolution.
Nowadays, information security is extremely important. According to the literature, the key remains fixed during the transmission, increasing the risk of frequency attack in the situation of redundant message transmission. First, we’ll look at how symmetric key-based cryptosystems handle keys as key sizes grow larger, and what that means for the future.
Later, we’ll show a strategy in which the key is created to change from session to session so that even if the hacker cracks the key of the session I it won’t work for original message extraction in sessions i+l and onwards. We may also improve the security level by applying a variability notion to the message and employing an optimal function to ensure that the data is received accurately by the receiver.
Another topic covered in this chapter is the parameterized approach to shared key computing. In this section, we discussed a method of key creation that does not require the transmission of the complete key via the communication channel. As a result, rather than sending the complete key, we will only send the parameters. We compute a result based on a certain function involving those parameters, and the receiver will do the same.
The beauty of this section is that, despite the fact that the sender and receiver employed two separate functions with identical parameter values, the outcome is comparable, and thus that is the shared key used for communication between them. As a result of our original contribution in this section, we may deduce that in cryptography, the complete key does not need to be sent to the receiver.
The scope of what is covered in this section is expanded to include the development of a patent if the key is generated using a reversible function like XOR. Symbolically: Y— X e K, If we get the value of Y and know K then we will get X from X* Y. This leads to scope for investigation of another similar reversible function.
Analysis of a fixed-length convention key with rising key size
The background for the AVK-based cryptosystem will be discussed in this section. To do so, we’ll look at some popular symmetric cryptic algorithms and show how they work in terms of encryption and decryption, using a web-based tool called SGcrypter, which was created specifically for this purpose, and we’ll find the most efficient algorithm among DES, 3DES, BlowFish, and TwoFish. To improve security, this approach increases key size.
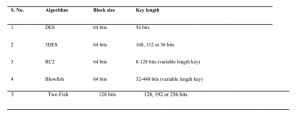
Because there are numerous symmetric key algorithms for performing the identical work of cipher creation and processing, the question of which one is better arises. Which is the safest and most energy-efficient? In symmetric cryptosystems, the current state of the art for boosting security is to increase the bit size from 32 to 48 bits, or to 56, 64,128 or 256 bits, or beyond, although this sacrifices computation speed and storage costs.
To select the most efficient or optimal symmetric-key method from a list that includes DES, 3DES, BLOWFISH, and TWOFISH. With an online tool to analyses or compare for decision making, one may be able to get the most out of them.
Automatic Variable Key based Cryptosystem
Based on the previous sections’ discussion and consideration of tables 2, 3, 4, and 5, it can be speculated that, in addition to raising the key size to strengthen intruder decryption, one can employ Automatic Variable Key (AVK) cryptosystems, in which the key is made to vary from session to session. This solution does not compromise the algorithm’s security, nor does it require more calculation time or device power.
This method is more secure because, even if a cryptanalyst or hacker obtains the previous session’s key, the key will change in the following session, making it theoretically impossible to recover the original message. Furthermore, because this technology utilizes relatively less power, it consumes less energy. Furthermore, the session-by-session key unpredictability makes it resistant to vulnerability.
Even if a hostile attacker compromises session i’s key, it will not be valid for original message extraction in sessions (i+l) and later. Another feature of AVK is the computation of a shared key using only parameters, which allows for a key generation without sending the complete key across the communication channel. As a result, rather than sending the complete key, the algorithm will simply send the parameters.
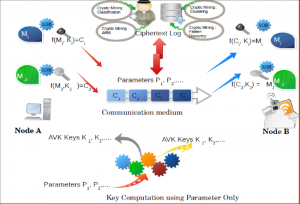
Figure 2 depicts the full framework. In fig. 2, the transmitter (node A) and receiver (node B) construct a key using some specified parameters that are passed to a function that processes them. The beauty of this section is that, despite the fact that the sender and receiver employed two separate functions with identical parameter values, the outcome is comparable, and so this is the shared key that they use to communicate.
The production of a function is also covered in this section, as long as the key is generated using a reversible function like XOR, i.e. X xor K=Y. Where d stands for a message, K for key, Y for cipher, and xor for encryption. If receivers gets the value of Y and K, he/she will get plain-text, X, because xor Y. This leads to an investigation for the feasibility of another similar function. In this research, we also presented the idea of cipher generation, which is based on a formula for key generation from session to session and a j integer in the form of 2m (where m O, 1, 2.. n total number of frames obtained from dividing the original message).
As a result of the aforementioned equation, if someone calculates the cipher using the values of j as l, 2, 3, 4, Then, on the receiver’s side, during cipher retrieval, the receiver must do a similar process but with the opposite sequence value of the cipher (i.e., 4, 3, 2, and l). The ciphers are created without the use of a key from the original data. This will show my contribution to the concept of cipher generation, as well as my original contribution to the concept of cipher generation.
A framework for an AVK-based symmetric key cryptosystem can be created using the aforementioned concept. Figure l depicts the operation of an AVK-based cryptosystem and its dissection from the perspective of a cryptanalyst. Node A (Alice) has a message Mi in session I which she encrypts with the session’s key, say Ki, and sends as cipher text Ci.
The encryption text is transmitted through a communication medium to a recipient Node B (Bob), where the plaintext information is recovered when the reverse procedure is completed at Node A. Now, A (Alice) has a new message Mj in session j, which she encrypts with the session’s key, says Kj, and sends as cipher text Cj. The encryption text is sent through a communication medium to a recipient Node B (Bob), where the plaintext data is recovered when the reverse procedure is completed at Node A.
Both sessions with distinct keys will be secure in this manner. The diagram also shows that the key is not exchanged through the communication channel, but rather in terms of parameters. The key is safer in this method, and it adds a layer of security. A hacker or cryptanalyst may be able to obtain the encrypted text log. It can be mined to derive patterns from the logs, and a number of tools and procedures can be used to exploit flaws or capture sensitive data.
Parameterized AVK based Cryptosystem
The technique of key computation utilizing only parameters is also highlighted in the bottom portion of the framework (Fig. 3).
By exchanging parameters through a communication link, Alice and Bob will compute keys. The following algorithms can be used to demonstrate this.
4 Key-Alice Algorithm-I parameters (parameters p1, P2)
{
- Sense parameters p1, p2;
- Compute the key for information exchange by:keyi =
- Sense the information to exchange=Di;
- If(mode==transmit)
Generate Cipher text C I =f_Encrypt(Di, key i);
Transmit Ci;
- else
Receive Plain text p i = f_Decrypt(Di,keyi);
Use p i;
}
{
- Sense parameters p1, p2;
- Compute the Arithmetic Mean A.M=(p1+p2)/2;
- Compute the Harmonic Mean H.M.-2* p1*p2 /(p1+p2)
- Compute the =
- If (mode==transmit)
Generate Cipher text C I =f_Encrypt(Di, key i);
Transmit Ci;
- else
Receive Plain text p i = f_Decrypt(Di, key i);
Use p i;
}
As a result, the AVK-based system performs as expected while consuming the least amount of power. A lot of publicly available evidences in the literature suggest that increasing the key length is not a smart idea because it increases computation time and power consumption.
When the key size is set and modified from session to session, the system not only increases the key size, but also aids in energy efficiency by using small-sized parameters. The study of cryptosystems from the perspective of a hacker or cryptanalyst will be covered in subsequent sections of cryptic mining.
Strengths and weaknesses of symmetric and parameterized cryptosystems analyzed
From a cryptanalyst’s perspective, we’ll look at the strengths and weaknesses of the AVK-based cryptosystem in this section. We’ll find out how resistant the AVK technique is to cryptanalyst and hacker attacks.
What are the odds that the system is vulnerable, and how can the loss or predictions be minimized? The technique will be explained in further detail in the following sections.
Investigation of an algorithm for detecting a symmetric method’s flaws
Cryptic Mining is based on the investigation of data mining techniques’ application in the cryptography sector. The Cryptic Mining toolset is a collection of approaches for tracking activities. Originally, data-mining approaches were concerned with information extraction at the application level or for individuals or organizations’ business and commercial needs.
A Low-level information domain is referred to as “cryptic mining.” By assisting cryptanalysts, this knowledge area improves the security level of information and the power of cryptic algorithms. Automated methods that intelligently exploit patterns among cipher-text, plain-text, key size, key life-time, and log of partially recovered plain-text-cipher text derived information can be built to strengthen the crypto-system.
The cryptic mining domain believes that cipher texts on the network or in encrypted files/logs aren’t completely random and show some patterns. These patterns could be beneficial for exploiting flaws in mining algorithms.
[Definition] Cryptic Mining: A class of mining algorithms used specifically for auditing a cryptosystem in order to determine the degree, strength, and weakness of constituent algorithms, as well as the algorithm class to which they belong. It has dedicated and specialized algorithms for mining binary data, cipher text logs, and cryptosystem outputs. The following naïve tasks are supported by the class of cryptic mining algorithms.
Cryptic pattern discovery
In theory, cipher text created by any cryptic algorithm should be completely random however, this is not always the case. They are created utilizing a fake process or mathematical equations that have some pattern identification. Finding weaknesses in the algorithm or procedure by exploiting or applying these patterns is a difficult undertaking. For cryptic pattern finding, a set of algorithms for pattern or sequence identification will be studied. Pattern recognition could be beneficial for determining correlations between plaintext, cipher text, key generation mechanisms, and historical trends between these elements from one cryptosystem to the next.
Cryptic Classification
This approach is useful for classifying and distinguishing encrypted text in order to reduce the effort required for hackers or cryptanalysts to dig up information about the encoding algorithm or retrieve the plaintext. On the other hand, it may be beneficial to categorize cipher text packets based on key patterns, key size, and cipher type in order to exploit trends or coincidences among them. One of the most important applications might be the creation of a rapid and precise malware detection system for the Honey-net system.
Cryptic association rule discovery (Cryptic ARM)
Cryptic ARM: In theory, each key in a cryptosystem should be independent of the others, but this is not always the case. For example, in the case of parameterized keys, some parameters (used in earlier key production) may be reused in current or future keys. Cryptic association rule discovery may be useful for identifying relationships or associations among keys (or a portion of a key as parameters) formed in multiple sessions and dependencies, as well as to investigate common patterns of key formation utilizing parameters. In most cases, one key will appear without the other however, their generation may be linked due to a formula or method for key generation.
Cryptic Clustering
In terms of cluster size, classified ciphers may be beneficial for determining the degree of vulnerability in cryptic clusters. By grouping cipher text into different clusters based on similarity of key patterns, key length, cipher type, and other attributes, important parameters for identifying cryptosystem flaws and strength can be expressed, and therefore auditing can be done.
Cryptic forecasting
A hacker or cryptanalyst system can be constructed based on historical cipher-log and training set information to forecast system behavior based on key experience. As a result, we can officially define cryptic mining as a set of approaches for presenting/ providing plausible associations in plain-text, cipher-text, or both (not based on cause-effect relationships). Furthermore, cryptanalysts must uncover correlations and establish what is significant, not just between key and key length, but also between the numbers of parameters utilized for key computation, key strength, cipher text-plaintext relationship, and running encryption/decryption key.
Aiming for symmetric and parameterized cryptosystems in the future:
Enabling Cryptanalyst with improved tools is in high demand for detecting cryptosystem vulnerabilities and weaknesses. Cryptanalyst is interested in extracting useful guesses from a large corpus of ciphers in polynomial time for finding original information. Cryptanalyst may have gathered a vast database and corpus of ciphers and hash files. When a cipher text is inserted into this dataset, it may be mixed with ciphers generated from a variety of other schemes, such as key size, protocol, type of ciphers generation algorithm, degree of key space information exposure, and a variety of other data about plaintext, cipher text, and their relationship. The cryptanalyst may devise a system that categorizes, sorts, and groups cipher types.
Conclusion
Cryptic mining attempts to apply and employ data analysis from session records in order to identify patterns connected to attacks.
Finding the warning signs of an attack can aid in the development of effective prevention tools and approaches, and observing the action associated with an assault can aid in the identification of vulnerabilities to control and potential damages.
This introduces new secure information exchange over the network strategies that may be applied to both wired and wireless systems. Although the AVK technique is said to be secure, parameter-based communication would provide an additional layer of security to the system. The use of an association rule to forecast likely parameters from parameter space may provide suggestions for future parameters to anticipate key. However, because both the amount of parameters and the session key are flexible and change from session to session, the system’s security is not compromised.
In order to progress and learn Cryptic mining gathers data for training from a variety of sources. It makes an attempt to apply and use data from session logs to identify trends linked to attacks. Finding the warning signs of an attack can aid in the development of effective preventative tools and approaches, and witnessing the action associated with an assault can aid in the detection of vulnerabilities and potential damages.
Also read
- what are the row spaces, column spaces and null spaces in Linear Algebra?
- How to solve system of linear equations in Linear Algebra?
- what is the vector space in linear algebra? vector space example
- How to test the given vectors are linearly independent or not?
- What are the matrices and their types ?
- Finding Eigen Values and Eigen Vectors using MATLAB
- How to diagonalize a matrix? Example of diagonalization
- What are the shortcuts for finding the determinant of a matrix?
- What are the Block Matrices?
- what are the examples of scalar and vector quantities?
- How to perform similar matrices transformation?
- How to find the basis of a vector space V?
- what are the eigen values and eigen vectors? explain with examples
- What are the nodal incidence matrices?
- What is the span of a vector space?
- Study of Linear Transformation and its Application